Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Exchange Team Blog
You Had Me at EHLO..
URL
Copy
Options
Author
invalid author
Searching
# of articles
Labels
Clear
Clear selected
administration
All Posts
Announcements
Calendaring
Client Access
community
Compliance
Deployment
development
directory
Documentation
Events
Exchange
Exchange 2007
Exchange 2010
Exchange 2013
Exchange 2016
Exchange 2019
Exchange Online
High Availability
History
Hybrid
mailbox
managed availability
Microsoft
Migration
Mobility
Office 365
On premises
Outlook
OWA
Planning and Architecture
Protocols
scripting
Security
Setup
Storage
Tips 'n Tricks
tools
transport
Troubleshooting
Unified Messaging
Virtualization
Options
- Mark all as New
- Mark all as Read
- Pin this item to the top
- Subscribe
- Bookmark
- Subscribe to RSS Feed







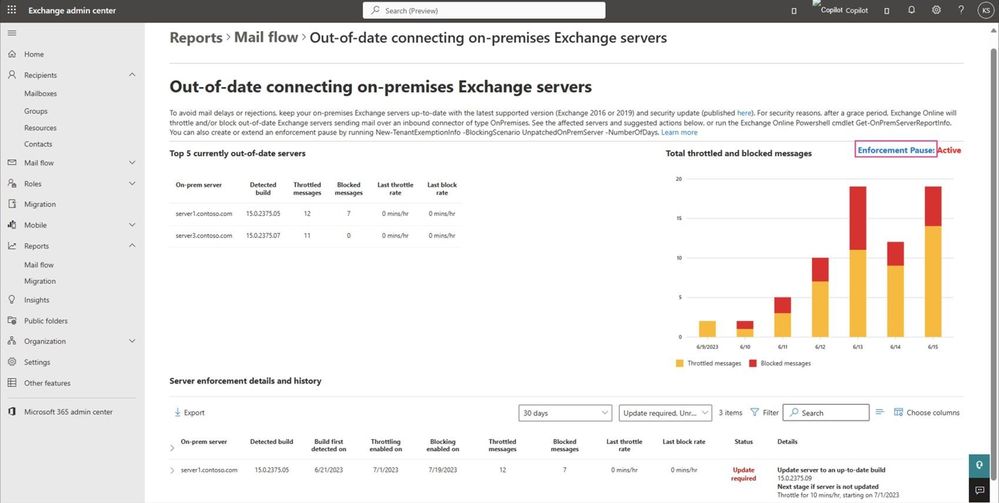
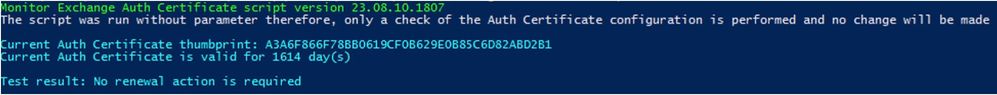

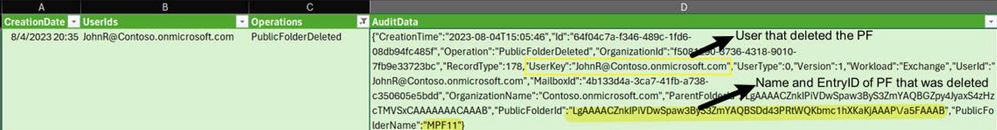


Latest Comments