Password Synchronization between Windows and UNIX Part I
Many a times we come across scenarios where organizations need a way to ensure that a particular user logging in different operating systems (UNIX and Windows to name) and changing his password. Unless there is a mechanism in place to make that password consistent across different environment he will end up keeping multiple passwords and the end result is definitely not going to be a pleasant experience J
Identity management for UNIX (and the previous version SFU 3.5) comes with a component called Password Synchronization to address this scenario; needless to mention this component does take away a great amount of administrative overload when put in place properly. I put the word properly to echo the considerable amount of planning we need to do before we can actually put this component to work for us.
Basically we need to understand the scenarios that call for such implementation. We will be discussing the possible ways to configure password synchronization here.
In its simplest form; say we have a Windows and UNIX system and the authentication mechanism is local to the systems. The only common objects between them that we have a user (say user_wu) having same name in both the systems and needs to login in both the systems. Of course, this user does not want to remember different passwords to login to different systems; so we are looking for a way to push his password to other system when changed from another and vice-versa. And this called as two-way password sync.
Before we jump into the configurations steps; let’s list out few basic things we need to remember. The first of all is the compatibility of the components of Password Synchronization.
In case of Services for UNIX 3.5
Two-way password synchronization is supported on UNIX computers running any of the following operating systems:
· Hewlett-Packard HP-UX version 11i
· IBM AIX version 5L 5.2
· Red Hat Linux version 8.0
· Sun Microsystems Solaris versions 7 and 8 running on Scalable Processor Architecture (SPARC)–based computers
In Windows 2003 R2; the Password Synchronization that comes with Identity Management for UNIX:
Two-way password synchronization is supported on UNIX computers running any of the following operating systems:
· Hewlett-Packard HP-UX version 11i, 32-bit environment
· IBM AIX version 5L 5.2, 32-bit environment
· Red Hat Linux versions 8 and 9, 32-bit environment
· Sun Solaris version 8 running on x86-based computers and Scalable Processor Architecture (SPARC)–based computers, and Solaris version 9 running on SPARC–based computers. The 32-bit environment has been tested on SPARC-based computers.
The download link for SSOD package for Windows 2003 R2 is www.microsoft.com/downloads/details.aspx?FamilyID=2ba5c443-d972-4b13-81ef-8ad20f779f51&displaylang=en
In Windows 2008; the list of supported UNIX environment is some way updated:
Password Synchronization supports synchronization with UNIX computers running any of the following operating systems:
· Hewlett Packard HP UX 11i v1
· IBM® AIX® version 5L 5.2 and 5L 5.3
· SunSM Microsystems Solaris™ 10, Scalable Processor Architecture (SPARC)-compatible versions only
· Linux
o Novell® SUSE® Linux Enterprise Server 10
o Red Hat® Enterprise Linux® 4 server
The package can be downloaded from www.microsoft.com/downloads/details.aspx?FamilyId=8EDBE153-B4F3-4DF6-B0AD-54A43C02CA29&displaylang=en
On the Windows side; password sync component can be installed on a standalone system or on a domain controller. In case on Windows XP and Windows 2003; Password Synchronization component can be added from SFU 3.5. We need “Administrative” privilege to carry on this installation.
Let’s take a look at the configurations on the Windows side.
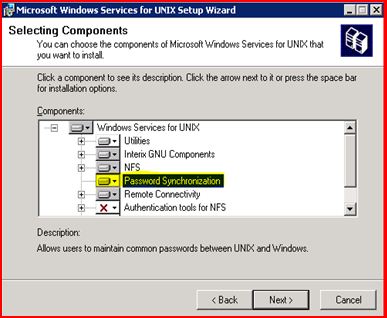
On SFU 3.5; the screen looks like this:
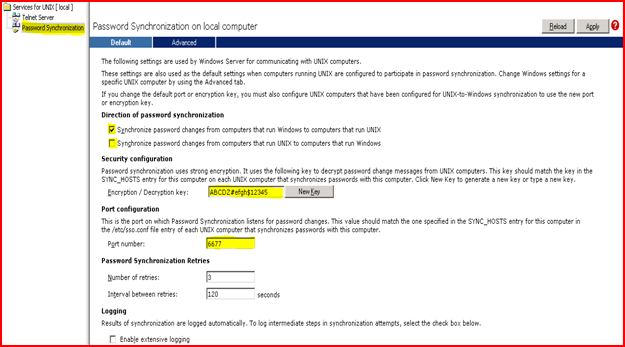
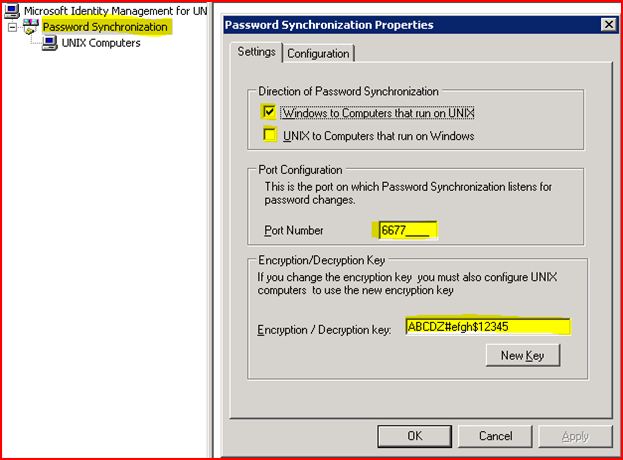
· The direction of password synchronization if one-way (Only from Windows to UNIX) or two-way (From Windows to UNIX and vice-versa)
· Encryption / Decryption key to make password human unreadable; recommendation is to change the default key
· The port no. on which a daemon will be running to capture any password replication request coming from Windows side; again the recommendation is to change the default value.
The list above mentions the essential configurations we need to care about.
On a Windows 2003 R2 box this looks almost similar; but available as properties page of Password Sync.
Now, the push the password from Windows side to Linux systems we need to perform the following steps:
Note: The steps will be some what different depending on the UNIX operating system. I will mention the parts that need to be taken care.
The unix\bins folder of different package contains the components for password synchronization. So, we need to:
Copy the appropriate source binary file from \unix\bins to /usr/bin or /usr/local/bin on the UNIX computer, and change its name to ssod. The name of the source binary file depends on the version of UNIX you are using.
If the computer is running Hewlett-Packard HP-UX, the source binary file name is ssod.hpx.
If the computer is running Red Hat Linux, the source binary file name is ssod.rhl.
If the computer is running Sun Microsystems Solaris, the source binary file name is ssod.sol.
If the computer is running IBM AIX, the source binary file name is ssod.aix.
2. Using a binary file-copy method such as File Transfer Protocol (FTP) to avoid corrupting CR/LF (carriage-return/line-feed) pairs, copy Sso.cfg from \unix\bins from the ppackage to /etc on the UNIX computer, and change its name to sso.conf.
3. Open sso.conf with a text editor.
4. If you have changed the default encryption key, edit the following line to specify the new default key. This value must match the default key specified on all domain controllers with which this computer will synchronize passwords:
ENCRYPT_KEY= encryptionKey
5. If you have changed the default port, edit the following line to specify the new port. This value must match the port number specified on all domain controllers with which this computer will synchronize passwords.
PORT_NUMBER= portNumber
6. Edit the following line to specify one domain controller in each Windows domain with which the computer is to synchronize passwords. If you have specified a nondefault port number or encryption key for the UNIX-based computer when configuring Password Synchronization on the Windows domain controllers, specify that value where indicated; otherwise, leave the value blank:
SYNC_HOSTS=( domainController[ , portNumber [ , encryptionKey]] ) ...
Each entry in the list must be enclosed by parentheses (the "(" and ")" characters) and separated from the next entry by a blank space.
8. Set the file permissions of sso.conf to read/write for the root user only, and deny access to all other users.
9. If the computer is running Linux, copy /etc/pam.d/system-auth to /etc/pam.d/ssod; else we can skip this step.
One last step on *NIX box to start the ssod deamon using the commad: ssod –v
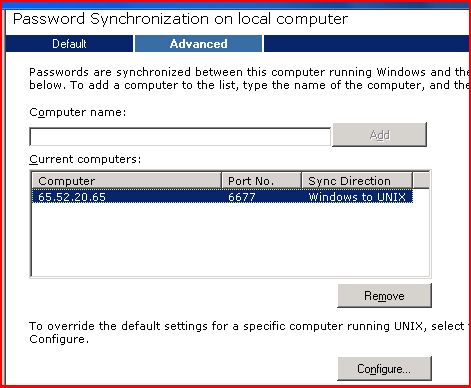
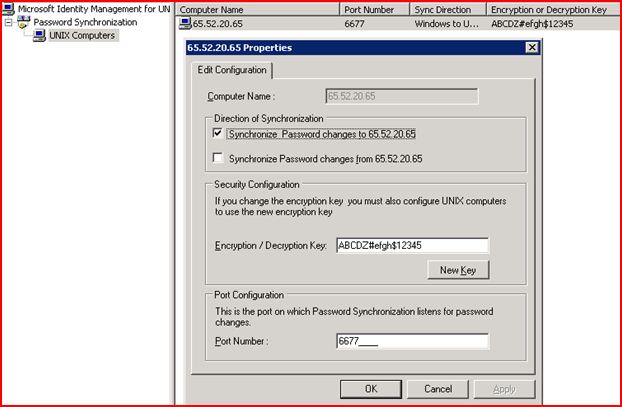
Back on windows side, we need to add the *NIX box in the password synchronization console:
On SFU 3.5:
On R2:
Now, we are all set the push the password from Windows box to *NIX systems; let’s reset the password for the user user_wu, and we should be able to see the events mentioning that password synchronization was done successfully to the user on the *NIX box.
In the next part we will discuss on synchronizing the password from UNIX to Windows box.