UAG and AD FS are Better Together – Publishing Non-Claims Based Applications
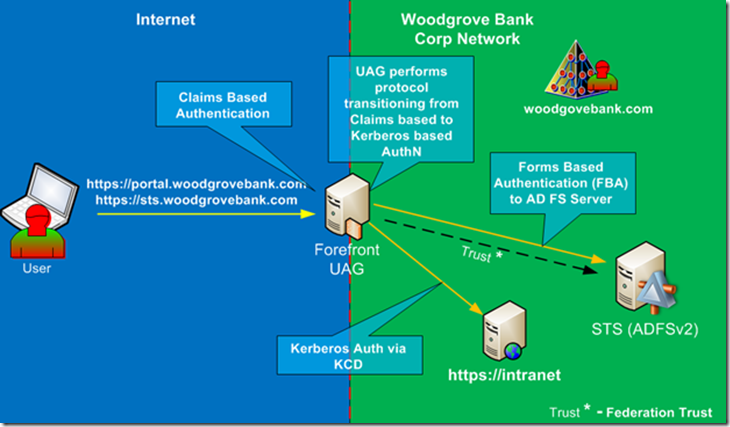
In article “UAG and AD FS are Better Together – UAG as AD FS Proxy” we explored how user authenticates to UAG portal via claims based authentication and then accesses claims based application published via UAG portal. But what if published application does not support claims based authentication, after all how many applications out there that do? Fortunately, UAG is capable to publish and provide SSO experience for non-claims based applications as well. The caveat here is that they must support Kerberos authentication. If you remember this “UAG and ADFS are Better Together– Strong Authentication” topology where we provided access with strong authentication, we configured KCD authentication between UAG and AD FS server. In this topology the configuration is slightly different but concept is the same. Instead of doing KCD between UAG and AD FS, we’ll need to configure KCD between UAG and the target application.
UAG is smart enough to transition from the claims based authentication and request Kerberos ticket from AD Domain Controller on behalf of the user. During application configuration you’ll need to specify what claim you’d like to use as a leading value to get the Kerberos ticket. UPN is a good choice. Also, the proper SPN must be configured in AD for the target application.
Figure 1 shows main aspects of this configuration and Figure 2 provides high level authentication steps of how this works. It is very similar to the previous configurations, just in slightly different order.
Figure 1
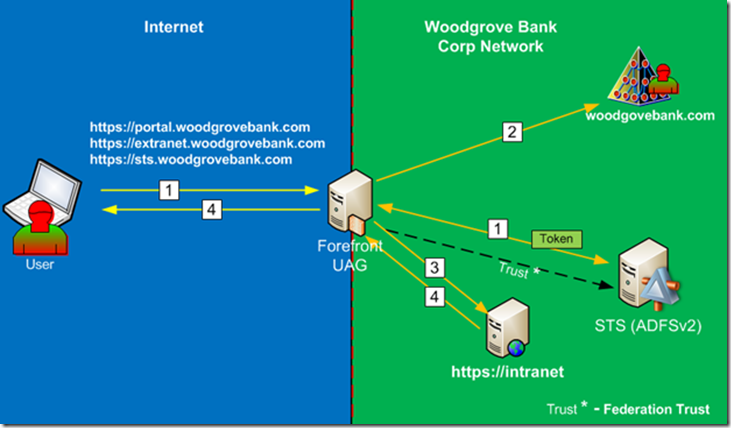
- First, user must authenticate to the portal with SAML token, this is done via authentication to the backend AD FS server.
- When user tries to access published application that was configured with Kerberos Authentication, the UAG server will contact AD Domain Controller and will get Kerberos Service ticket for the target application. It will use the claim value that was configured with this application in its request to Domain Controller.
- Then UAG will send Kerberos ticket to the target application. Application will use the Kerberos ticket for authentication and authorization decision.
- If authentication was successful target application will allow access to the end user.
Figure 2
This configuration has similar constraints as was discussed in topology with Smart Card authentication, they relate to the Kerberos constraints. In this configuration application servers must reside in the same Active Directory Domain as UAG server (obviously that means that UAG must belong to AD domain) and the user account must be in the same Active Directory Forest as UAG server as well. Also, there are requirements on the Domain and Forest Functional level, it must be at least at Windows 2003 level.