What’s New, R2? – Networking: 802.1X Authentication
You can play around with and test the features I will be discussing in this series by download the Windows Server 2012 R2 Preview here -
Networks. Whether wired or wireless, we have to have them to connect all of the various pieces of our infrastructure together. Not only do we use them to connect clients to servers and servers to other servers on our Intranets, they are the backbone of how we transfer the massive amounts of data from point to point on the Internet. We virtualize entire networks within highly virtualized systems. We use networks to connect our on premise infrastructure to cloud based infrastructure. Networks are being used more and more for connecting to remote storage. Without networks, it all grinds to a halt.
I don’t want to trivialized other aspects our infrastructure, but it is safe to say that networks, because they can have public access points via an RJ-45 port in the reception area (not to mention the hundreds scattered around the rest of the office), and because our WiFi networks extend beyond the physical boundaries of our buildings, act as the door to everything else. If we don’t secure that door, then we are giving away a lot of front-line access to the rest of what we have inside.
A variety of devices, techniques and protocols have been introduced over the years to help IT Pro’s managed that initial access to the network. For this article, I am going to focus on 802.1X Authentication for Wired and Wireless Access.
What is 802.1X Authentication?
IEEE 802.1X authentication provides an additional security barrier for your intranet that you can use to prevent guest, rogue, or unmanaged computers that cannot perform a successful authentication from connecting to your intranet. Standard wired Ethernet give administrators control over physical port placement as well as the ability to physically enable/disable the port. Network admins can also control access virtually through switch controls. However, WiFi networks are by their very nature accessible wherever the signal reaches. So we needed a means of extending more control over WiFi access.
802.1X gives network administrators the tools to force a wireless client to submit a set of credentials that have to be validated before we allow them to send and frames to/from the intranet. These days, this is typically this is managed a Network Policy Server (NPS) and certificates. The NPS lets you centrally configure and manage network policies by using the following three components: RADIUS server, RADIUS proxy, and Network Access Protection (NAP) policy.
Over time, network administrators wanted this same control over wired connections as well. This simplified managing network access across all connectivity points, wired or wireless. Fortunately, this capability has been around since the Windows Server 2008 timeframe.
We have made improvements to the implementation and control in since that time and Windows Server 2012 introduces some improvements to the 802.1X implementation for both wired and wireless connections.
What's New in 802.1X Authenticated Wired Access for Windows Server 2012 R2
With the explosion of Bring Your Own Device (BYOD) in the last few years, network administrators have to balance granting access to non-domain joined devices and maintaining access control. Users want a more seamless experience even if their Windows device isn’t domain-joined. Network admins are responsible for ensuring that they aren’t giving away too much access and control.
If you have deployed password-based 802.1X authentication methods for wired and wireless connections through Ethernet switches and wireless access points, users with non-domain joined computers and devices that are running Windows 8.1 Preview and Windows Server 2012 R2 Preview (and presumably with the RTM bits of the aforementioned) can bring their own devices to your organization and enjoy the advantages of password-based credential reuse.
This means users with non-domain joined devices can essentially do single sign-on (SSO). End users can provide their credentials the first time they connect to your organization’s network, then connect to all the resources they want to without being prompted repeatedly for their credentials, because the credentials are stored on the local computer for reuse.
Does that mean the credentials are cached forever?
No. For security reasons, when the user’s computer or device disconnects from the network, the stored credentials are discarded. They will have to provide their credentials again when they re-connect to the network.
There are some limitations/requirements though -
This feature is available for non-domain joined computers and devices that are running Windows 8.1 Preview and Windows Server 2012 R2 Preview (again, this should hold true for the RTM bits as well) when you have deployed the following authentication methods on your network.
- EAP with Microsoft Challenge Handshake Protocol version 2 (EAP-MS-CHAP v2)
- PEAP-EAP-MS-CHAP v2
- EAP-TTLS with EAP-MS-CHAP v2
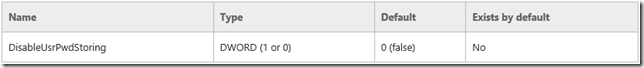
This feature is enabled by default for Windows 8.1 Preview and Windows Server 2012 R2 Preview. You can use the following registry key to disable or re-enable user password storing if you have previously disabled it. When this registry key is set to 1 (true) EAP methods do not store any credential information in Credential Manager:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Eaphost\Configuration
By the way, the above also applies to Wireless 802.1X access!!
Which leads us to……
What's New in 802.1X Authenticated Wireless Access in Windows Server 2012 R2
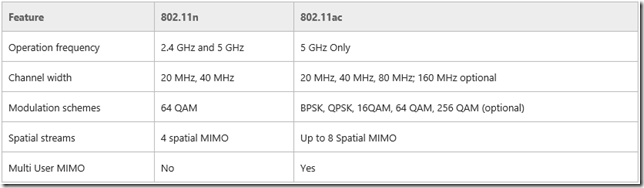
Windows 8.1 Preview and Windows Server 2012 R2 Preview support 802.11ac wireless access (note – WiFi access is disabled by default on all current Windows Server platforms. It is highly recommended you do NOT enable WiFi on servers). This standard provides higher speeds, throughput, reliability, and quality of WiFi communications. Below is a comparison between 802.11n and 802.11ac:
So there you have it! Nothing terribly earth shattering, but certainly some pieces that make it easier for network admins to accommodate BYOD and to provide a better experience to end-users without compromising access and control.
-Cheers!